Among the many types of cyberattacks, the most diverse methods, and the new unconventional methods, there are some that work covertly without the user knowing and above all without suspicion. Of course, these are the hardest to spot and fight, because almost always, they are allies: we’re talking about clickjacking.
Table of Contents
Clickjacking: meaning & definition

What is Clickjacking?
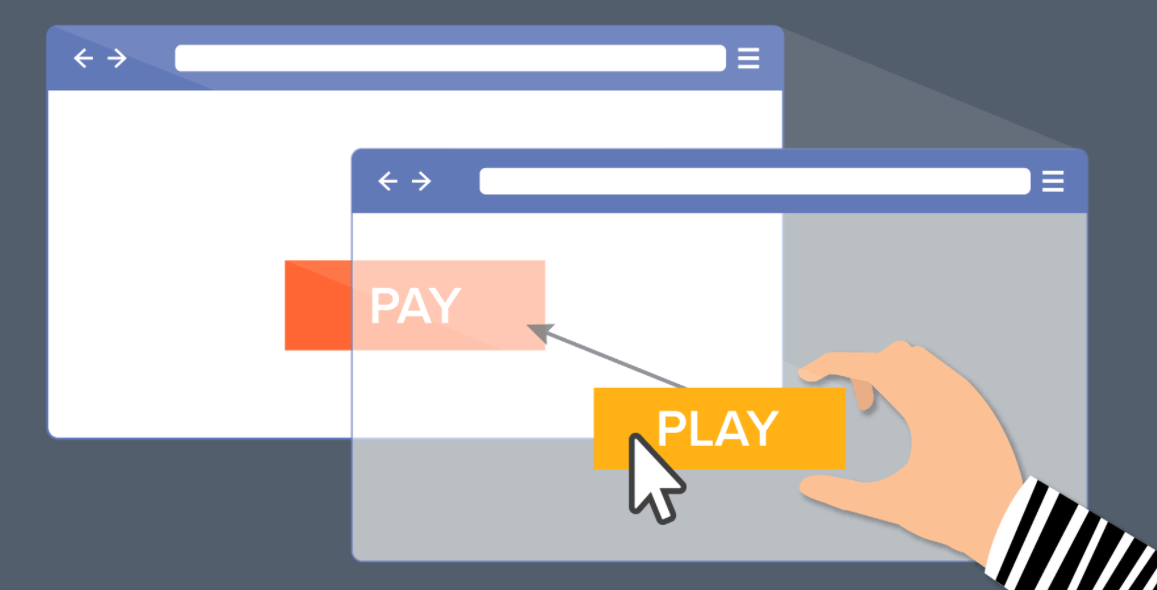
Clickjacking is an attack that causes an uninformed user to click on an element that is not visible on a web page or hidden by another element.
The goals that users attempt may be different, such as accidentally downloading malware, visiting malicious web pages, providing clues or sensitive information, transferring money, or purchasing products online.
Typically, clickjacking is done by displaying an invisible page or HTML element inside the frame at the top of the page the user is viewing. The user thinks he is clicking on the link and all the information that appears, but in reality, he is clicking on the invisible element in the extra page at the bottom of the page that is displayed.
In fact, a page that is not displayed may be a malicious or legitimate page that the user does not want to visit. For example, banking sites where money transfer operations take place are often the most sought-after targets, as is often the case.
Before continuing the discussion, let us recall that iframes are an HTML element, as reported by Wikipedia (from the English inline frame) in computer science. This is, in fact, the frame “anchor” on the page, which is the same as the normal frame, but by contrast, it is the (internal) element of the page, not the external one.
Clickjacking: A hypothetical Example
Below are some steps (A hypothetical example) you can take to begin the process of preparation for mediation.
1. The attacker creates a lucrative page that promises the customer great deals or very discounted products.
2. In the background, the attacker checks if the customer is connected to his banking site and if so, loads a screen allowing the transfer of funds using queries to enter the attacker’s bank details on the form.
3. The Bank Transfer page is displayed in an invisible frame at the top of the Benefit Offers page, with the “Confirm Bank Transfer” button perfectly aligned, for example to the “Search for Offer” button visible to the customer.
4. The user visits the page and clicks on the “Discover the Offer” button.
In effect, the user is clicking on the invisible frame and clicking the “Confirm Transfer” button. Funds will be transferred to the attacker.
5. The user is redirected to a page with information about the offer (not fully aware of what happened in the background).
This frivolous example shows how in a clickjacking attack, the malicious act (on the bank’s website, in this case) did not return to the attacker because the user did this while legally logging into their account.
From this, it is easy to understand the prevalence of triple verification codes, if not double, that keep monetary transaction sites from protecting themselves from such scams.
Types of Clickjacking attacks
Clickjacking types come in a variety of forms and are represented by a broad family of attack vectors and techniques commonly known as user interface recovery attacks.
Attacks can be divided into two macro-categories based on the overlapping content used.
Attacks based on “overlays” (the process of moving program code or other data blocks into main memory, instead of those already stored) have become very popular, and embedding pages in invisible Iframes is the most common technique. Is. Case. Again, there are several major categories of overlay-based clickjacking:
Complete Transparent Overlap: This is the method used when a carefully designed malicious page is overlapped on a transparent legal page (called a tool page) when the tool page is loaded in an invisible frame and the value is z – the highest index. One of the first high-profile clickjacking attacks, Adobe used this method against the Flash plug-in settings page to trick users into giving their computer camera and microphone access to Flash animations.
Clipping: For this attack, the attacker will override only the selected controls from the transparent page to the visible page. This means enabling different actions, such as covering buttons with invisible hyperlinks, covering text labels with misleading instructions, and replacing button labels with duplicate commands, depending on the target of the attack. , Or covering the entire legitimate page with fraudulent content, opening only one basic button.
Hidden overlap: This is the first method performed in the context of clickjacking. The attacker creates a 1 × 1 pixel frame containing malicious content and places it under the mouse cursor so that it is hidden from the cursor but any clicks are recorded on the malicious page.
Quick Content Replacement: Opaque overlays are used to cover target controls, only one second to register clicks are removed and replaced immediately. The attacker must predict the exact moment of the victim’s click, but with a little understanding of the computer user’s habits and psychology, it’s much easier than it sounds.
Other macro-categories try to work without using clickjacking vulnerabilities to insert overlays. There are several options for attackers to deceive customers by clicking on unexpected checks:
Scrolling: The attacker partially scrolls through a valid dialog box or any other element of the web page so that the user can only see specific controls. For example, a warning dialog can be scrolled across the screen so that only the OK and Cancel buttons appear, leaving the attacker with a malicious prompt text so that the buttons apply to the message and not to the alert.
Shifting: This attack requires quickly moving the trusted dialog box (or another UI element) under the cursor when the user is focused on clicking on other innocent elements. If it works, the user will naturally click on the changed control before realizing that something has changed. With faster content replacement, the dialog box can be moved quickly after the attacker clicks to avoid being detected.
Drag-and-Drop: Although many clickjacking attacks are clearly focused on intercepting clicks, drag-and-drop vulnerability can be used to motivate the user to perform a number of other actions, such as dragging web invisible text to remove a form or exposing sensitive personal information to an attacker.
There are also other dynamic interactions between the user and the elements of the web page, which are made possible by combining elements of JavaScript, which provide countless options to prompt users to perform unexpected actions.
Because clickjacking attacks take advantage of the user’s trust in the content and controls displayed, they can be difficult to detect automatically.
Clickjacking attack prevention techniques
Below we are going to suggest some brief tips to protect against clickjacking attacks, which we have learned in this article, which are very difficult to detect and prevent.
Among the countless implementations available to users, we have found different and different security methods that can be set on both the client-side and the server-side.
On this gap, we are going to analyze whether appropriate action should be taken.
Server-side clickjacking prevention
There are many clickjacking attacks on fake legitimate websites. The attacker can clone the website and modify it with links to other pages, so make sure the web pages are not included in the <FRAME> or <IFRAME> tags.
There are two ways to do this:
1. Specify the appropriate content-security-policy command: Content Security Policy (CSP) is the most effective cyber security strategy against embedding web pages with its terms on the ancestor of frames. In addition to protecting the website from embedding iFrames, the content-security policy also protects websites from cross-site scripting (XSS), which is one of the most common cyber talks.
To apply for this protection, you must first make sure that the webserver is set up to back up the content security policy. Once CSP is implemented on the Website, the appropriate CSP frame-pre-command can be set without allowing the embedding of response headers. Frame-access prevents all domains from embedding the ‘None’ directive website in a single frame.
2. Specify not to allow x-frame-options directive: The X-Frame-Options response header specifies whether the browser is allowed to embed web pages in frames. The X-Frame-Options response header will eventually be obsolete and replaced with pre-frame instructions, so it should not be the primary protection method. To send the correct X-Frame-Options HTTP header from your website resources, you must set the command to “Reject”.
For example, X-Frame-Options Reject After setting the x-frame-options to the server-side rejection command, all attempts to load the website into one frame will be blocked. This is equivalent to the framework-primary self-command of the Content Security Policy, which allows web content to be generated only if the site shares the same source.
Client-side clickjacking prevention
Client-side clickjacking prevention is not as effective as the server-side prevention strategy. These methods should be implemented as a secondary option.
1. Frame busting script: The frame busting script prevents the website from running inside the frame. With the JavaScript add-on, you can specify how the browser will react when loaded into the page frame. A simple frame buster technique is to force the browser to reload the offset decoy web page in the upper window. By doing this, the website loads on top of the malicious iframe layer. Except for the allow-top-navigation attribute, the iframe containing a web page will not be loaded on top of the invisible page. With this protection, the attacker can allow the browser to execute scripts and submit the form. Frame busting scripts against clickjacking attacks are not recommended.
2. Install the browser extension: Anti-clickjacking browser extensions do not provide the best user experience because they disable all JavaScript on loaded websites. Many popular websites like Facebook, Twitter, and YouTube work in JavaScript and these extensions block its functionality. To place the JavaScript experience on trusted sites, you must specify a whitelist manually. The following is a list of JavaScript-blocking add-ons for different browsers:
- Chrome: ScriptSafe is an extension for Chrome;
- Mozilla Firefox: NoScript is an add-on for the Mozilla Firefox browser;
- Safari: JS Blocker is an extension for the Safari browser.
Also, in this case, it is possible to confirm that clickjacking is the best defense against attacks by following specific operating methods.
Conclusion
The conflict between developers and users over which perspective is more effective is open to the belief that prevention should come from developers and not from consumers, while others say there are many limitations to X-Frame being effective.
Ultimately, a combination of tools and incentives to encourage users to pay attention to the sites they visit and the work they do online is the best way to deter attackers before they take over. In this case, therefore, the structure remains an immovable pillar to protect one another.
Other Reads
What is Blogosphere & Who coined the term Blogosphere?
What is Augmented Reality or AR?
What is cloud computing with advantages & types?